What is Access control?
-
App Access Control is designed to restrict and manage user access to an app within Jira
-
Org Admins / Jira admins / Site admins - treated as Default Revyz app admin can access the app even if they are not part of any group specified in Access Control.
-
It ensures that only authorised users or groups can interact with the app, enhancing security, compliance, and data privacy.
Who can set the Access control?
-
Organisation Admins – Org admins have control over app permissions.
-
Site Admins - A Site Admin has the highest level of administrative control over the Atlassian site and its users.
-
Jira Admins – Jira admins have the highest level of control and can configure access settings.
Initial Access to Revyz App (Before Access Control Configuration)
-
Before custom access controls are configured for the Revyz app, the following users will automatically have "Default Revyz Admin" access, with the authority to set up further access controls.
-
Access is granted based on the highest available administrative group in your site, following this precedence:
-
Organisation (Org) Admins: If your site has an "Org admin" group, all members of this group will be Default Revyz Admins.
-
Site Admins: If an "Org admin" group is not present, but a "Site admin" group exists, all members of the "Site admin" group will be Default Revyz Admins.
-
Jira Admins: If neither an "Org admin" nor a "Site admin" group is present, all members of the "Jira admin" group will be Default Revyz Admins.
-
In essence, Revyz priorities administrative access in this order: Org Admin > Site Admin > Jira Admin. The first group found will be granted default administrative access to the app.
Different types of Permissions in Revyz app
-
App access - This permission defines if the group has access to the Revyz app.
-
Initiate backup - This permission defines if the users part of group has access to trigger a backup job.
-
Clone requester - Enable this to grant the selected group permission to initiate clone jobs. Only users in the group with this permission can trigger clone jobs.
-
Clone approver - Enable this to grant the selected group permission to approve clone jobs. The clone job will remain pending for approval until approved.
-
Cleanup initiator - Enable this to grant the selected group permission to approve clone jobs. The clone job will remain pending for approval until approved.
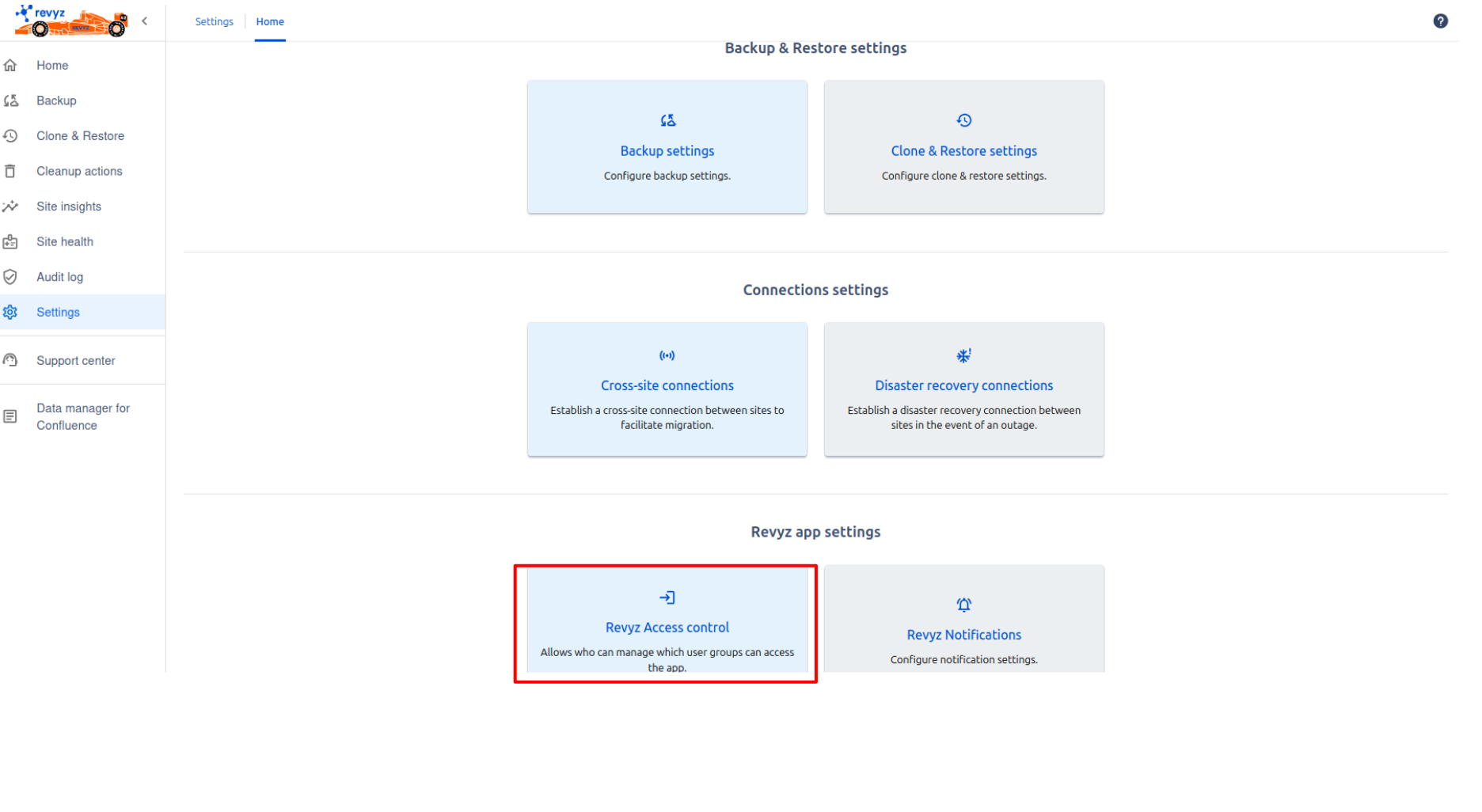
How to set Access control
-
Click on settings in the left navbar - > Click on 'Revyz access control' card under Revyz app settings.
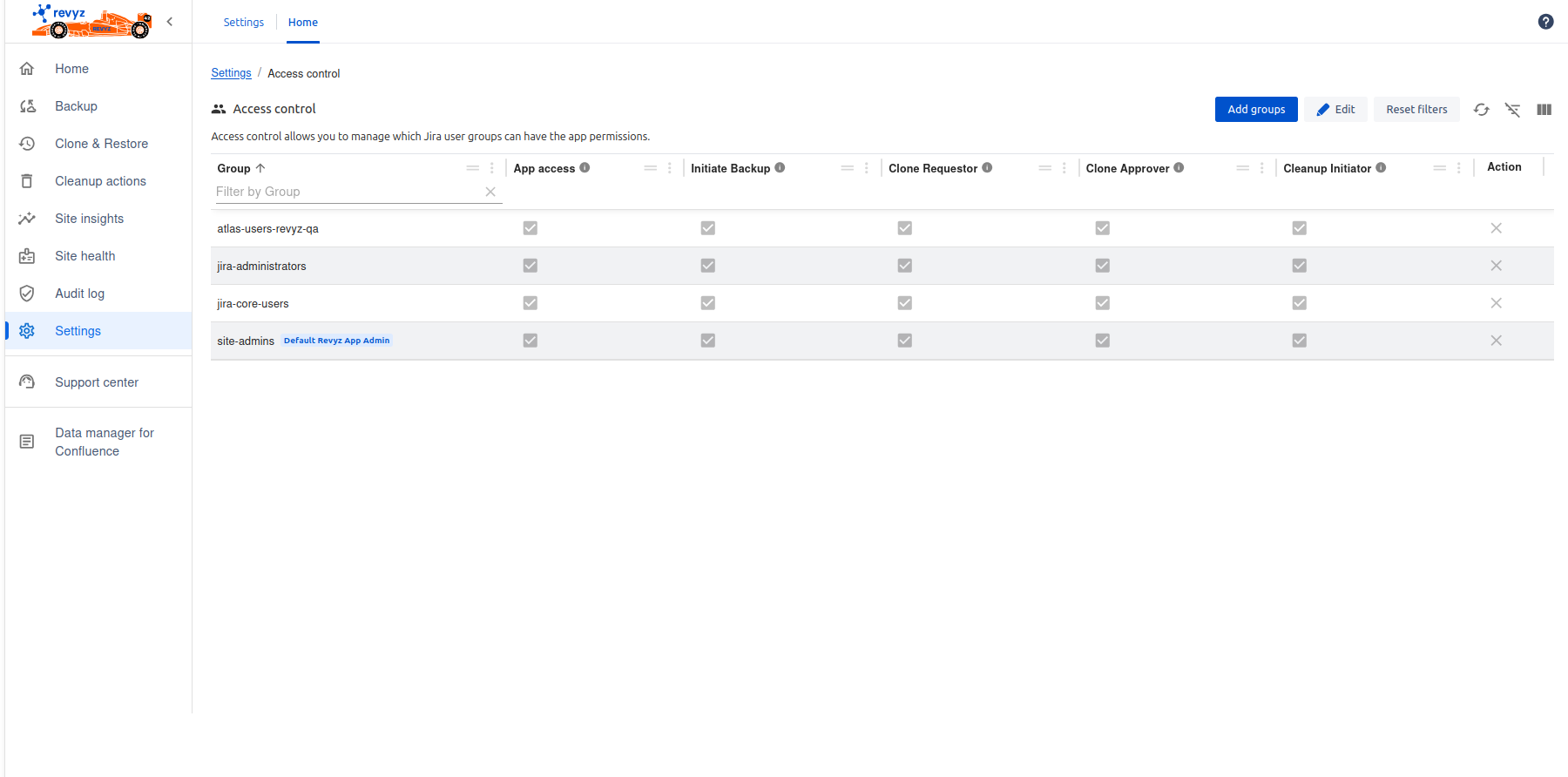
Granting Permissions to Groups in Revyz
-
You can easily manage who can do what in Revyz by assigning permissions to groups of users.
-
Instead of setting individual permissions for every single person, you can simply add a group, define what that group can access, and then all members of that group will automatically inherit those permissions.
-
Here's how it works:
-
Create or select a group: You can use existing user groups from your system (like "Jira-core-users").
-
Assign specific permissions: For each group, you decide exactly what they're allowed to do within Revyz app. For example, you could give one group permission to initiate cleanup jobs only, while another group might have permission to perform restores.
-
Members get instant access: Once you've assigned permissions to a group, any user who is a member of that group will automatically have those permissions in Revyz. If someone is added to or removed from the group, their Revyz permissions will update accordingly.
-
Default group permissions: When you add any group in Revyz, two permissions are automatically assigned to them and cannot be changed or removed:
-
App Access: All members of the group will have access to the Revyz application.
-
Initiate Backup: All members of the group will be able to start a backup.
This ensures that any user within an added group can always access Revyz app and initiate backups.
-
-
-
Clone Requester: This permission lets a user initiate clone jobs, which include cloning Jira configurations, projects, and asset configurations.
-
Clone Approver: Users with this permission can approve clone jobs that have been requested by others.
-
Cleanup Initiator: This permission allows a user to trigger cleanup jobs.