Last updated
Overview
Every care is taken by Revyz to protect personal data from incidents (either accidentally or deliberately) to avoid a data protection breach that could compromise security. This policy brings clarity to partners and customers regarding our approach to handle personal data breaches effectively.
Purpose
The company is obliged under the GDPR to have in place an institutional framework designed to ensure the security of all personal data during its lifecycle, including clear lines of responsibility. For more information, please see our Cloud Security Statement.(Cloud Security Statement )
Definition / Types of Breach
An incident in the context of this Policy is an event or action which may compromise the confidentiality, integrity or availability of systems or data, either accidentally or deliberately, and has caused or has the potential to cause damage to the company’s information, assets and/or reputation.
An incident includes but is not restricted to, the following:
-
Loss or theft of confidential or sensitive data or equipment on which such data is stored (e.g. loss of laptop)
-
Attempts (failed or successful) to gain unauthorized access to information or system(s)
-
Unauthorized disclosure of sensitive / confidential data
-
Human error
Responding to a Data Breach
Revyz’s response plan is as follows:
-
Confirm the Breach
-
Contain the Breach
-
Assess Risks and Impact
-
Report the Incident
-
Resolve the Incident and provide a postmortem report
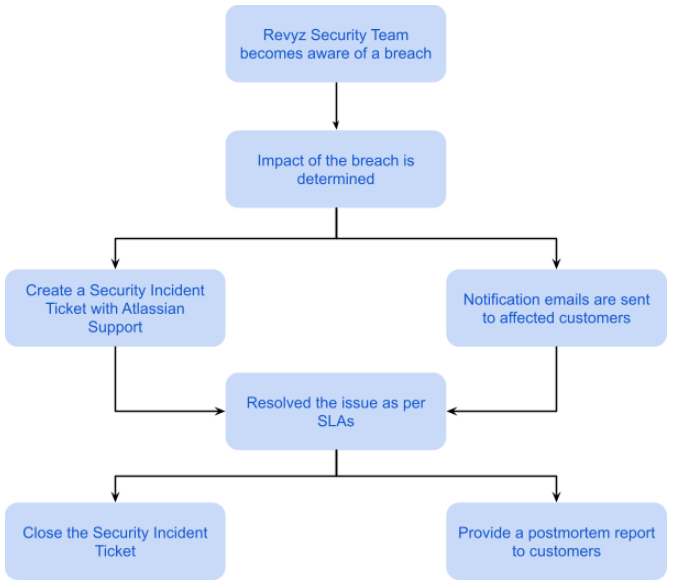
Security Incident Response Timeline
Revyz implements a 5-step security incident response framework with specific timelines driven by GDPR's 72-hour notification requirement. The policy emphasizes immediate containment within 8 hours, comprehensive risk assessment within 36 hours, and mandatory regulatory reporting within 72 hours of discovery.
The incident response timeline follows strict GDPR compliance requirements, with Hour 0 marking the discovery moment that triggers the 72-hour regulatory notification clock. The most critical actions occur within the first 4 hours, focusing on containment and initial assessment, while the 72-hour deadline serves as the absolute limit for supervisory authority notification.
Step 1: Confirm the breach (0-1 hours)
Timeline: Immediate response required within 1 hour of detection
The IT Security Team and Chief Information Security Officer (CISO) lead the confirmation phase, which serves as the foundation for all subsequent actions. This step involves verifying that a legitimate security incident has occurred rather than a false alarm, conducting initial triage and classification, and crucially, documenting the exact discovery time since this starts the GDPR 72-hour compliance clock.
Step 2: Contain the breach (0-8 hours)
Timeline: Immediate containment through 8 hours maximum from discovery
The Incident Response Team and Technical Lead assume control during containment, implementing immediate measures to prevent further damage or data exposure. This phase requires isolating affected systems, changing compromised passwords, revoking unauthorized access, and preserving evidence for forensic analysis.
Both short-term and long-term containment strategies must be deployed simultaneously. Short-term measures focus on stopping active threats, while long-term containment ensures the threat cannot resurface. Success criteria include verifying that the threat is contained and no further spread is occurring.
Step 3: Assess risks and impact (8-36 hours)
Timeline: Comprehensive assessment completed within 36 hours of discovery
The Risk Assessment Team, Data Protection Officer (DPO), and Legal Counsel collaborate to determine the full scope and implications of the incident. This critical phase involves calculating the approximate number of affected individuals, evaluating business impact and operational disruption, and most importantly, assessing risk to data subjects' rights and freedoms under GDPR.
Step 4: Report the incident to Customers (GDPR deadlines)
Timeline: Reporting deadlines with zero flexibility
Supervisory Authority Notification: Must be completed within 72 hours of becoming aware of the breach (GDPR Article 33).
Step 5: Resolve and provide postmortem (36 hours - several weeks)
Timeline: Ongoing resolution activities with postmortem completion within 2 weeks but could take longer depending on the issue at hand.
The Incident Response Team and Management oversee the resolution phase, which involves eradicating root causes, implementing permanent fixes, and restoring normal operations. This phase requires conducting a thorough lessons learned analysis, updating policies and procedures based on findings, and delivering a comprehensive postmortem report.